Differences between Business Email Compromise and Phishing or Spear Phishing
If you have never heard of Business Email Compromise (BEC), it is worth starting with a clear and practical definition:
1. Phishing broadly aims to harvest credentials or deliver malware at scale.
2. BEC targets business processes and funds through impersonation or inbox compromise, often leaving a minimal technical footprint.
At a high level, BEC occurs when fraudsters successfully impersonate a trusted business entity (for example: a vendor, an executive, or a business partner) and convince employees to transfer funds or disclose sensitive information. The attack succeeds not because of malware, but because it blends into normal business operations.
Phishing campaigns, in the other hand, are designed to deceive users into revealing credentials, personal data, or executing malicious payloads. They often rely on recognizable indicators such as suspicious sender addresses, generic greetings, artificial urgency, or links leading to unfamiliar domains.
In recent years, the adoption of generative AI has made both phishing and BEC more difficult to detect. AI tools lower the barrier for attackers and allow them to produce increasingly believable messages, especially to untrained recipients. While AI does not change the fundamentals of these attacks, it does improve their polish and scale.
What Is the Difference Between BEC and Phishing?
Phishing campaigns are typically volume driven. Attackers send large numbers of emails with limited personalization, prioritizing reach over precision. Some reconnaissance may be performed to improve credibility, but the messages are designed for mass delivery. The objective is usually credential theft, malware delivery, or initial access that can be monetized later.
BEC, on the other hand, requires preparation and patience. Attackers invest time in understanding the target organization, its payment workflows, approval chains, and communication style. Messages are tailored to specific individuals and often sent from compromised mailboxes or carefully crafted look‑alike domains. The primary motivation is financial—wire fraud, invoice manipulation, or payment redirection—though sensitive business data may also be targeted.
A practical way to frame the distinction is this:
1. In phishing, victims are counted in plural.
2. In BEC, victims are often singular, but the financial impact per incident is significantly higher.
Palo Alto Networks summarizes these differences effectively:
| Category | Business Email Compromise (BEC) | Phishing |
|---|---|---|
| Targeting & Personalization | Focuses on specific individuals or departments with financial authority or access to sensitive data. Highly personalized messages based on detailed reconnaissance. | Broad targeting with minimal personalization. Relies on mass messaging to reach as many recipients as possible. |
| Attack Complexity & Effort | Sophisticated attacks involving reconnaissance and, in some cases, AI/ML to mimic writing style and email behavior of the impersonated user. | Ranges from basic to complex, but often uses templated messages sent to many recipients. |
| Objectives | Financial gain through wire fraud or payment redirection; may also target sensitive business information. | Theft of personal information such as credentials or credit card data, leading to fraud, identity theft, or ransomware. |
| Method of Delivery | Delivered almost exclusively via email. | Delivered via email, but also through SMS (smishing), voice calls (vishing), or social media messages. |
| Scale & Scope | Targets fewer individuals, with a high financial impact per victim. | Casts a wide net to maximize victims, usually with lower value per target. |
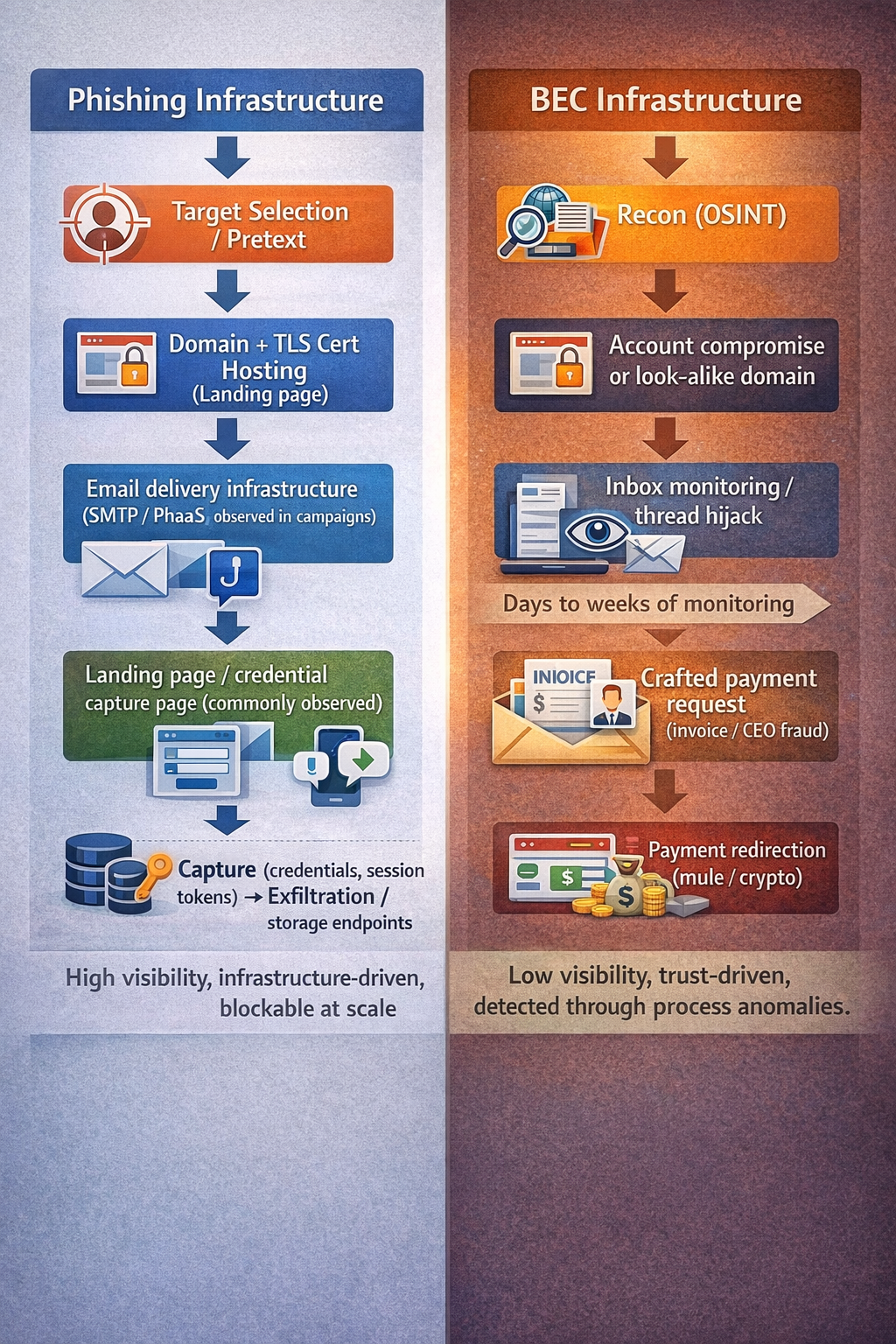
Infrastructure and preparation: BEC vs Phishing
Fraudsters and scammers choose their tooling and infrastructure based on the end goal. While both BEC and phishing rely on social engineering, the technical components and operational patterns differ significantly.
Social Engineering as the Common Denominator
Social engineering exploits human behavior rather than technical vulnerabilities. It works because people are conditioned to trust authority, follow procedures, and avoid conflict. Fraudsters use these instincts to guide victims toward clicking links, downloading files, approving payments, or disclosing confidential information.
Phishing Infrastructure
Phishing is one of the most scalable forms of social engineering. Its infrastructure is often modular and reusable, optimized for volume and rapid rotation:
Impersonation themes: attackers pose as banks, IT support, service providers, or delivery companies.
Credential pressure: password resets, account verification, or unpaid invoices are common lures.
Artificial urgency: threats of account suspension, collections, or service disruption.
Typical infrastructure components include:
Domains and TLS certificates: look‑alike or disposable domains with valid SSL to avoid browser warnings.
Mailing systems: SMTP infrastructure, compromised senders, or Phishing‑as‑a‑Service (PhaaS) platforms.
Landing pages: cloned login portals and credential harvesters.
Malware hosting and C2: payload delivery and command‑and‑control for malware‑based campaigns.
Obfuscation and evasion: redirect chains, URL shorteners, JavaScript obfuscation, and anti‑bot techniques.
Campaign management: dashboards for tracking clicks, victims, and conversion rates.
Monetization: credential resale, account takeovers, ransomware, or secondary fraud.
BEC Infrastructure
BEC operations are typically leaner from a technical standpoint, but heavier on operational discipline:
Account compromise or look‑alike domains: attackers hijack real mailboxes or register near‑identical addresses.
Long‑term reconnaissance: monitoring email threads to understand tone, approval flows, and vendor relationships.
Payment redirection: fake invoices, modified bank details, or pre‑staged mule accounts and crypto wallets.
Operational coordination: follow‑up emails or phone calls to reinforce legitimacy and timing.
Minimal technical footprint: malware is often unnecessary; trust and process gaps do the work.
Practical differences that shape infrastructure choices
Visibility: phishing generates noise—new domains, mass email bursts—which makes it easier to block once detected. BEC is stealthier, blending into legitimate communications.
Tooling: phishing relies on automation and kits; BEC relies on OSINT, compromised identities, and human judgment.
Monetization: phishing monetizes at scale; BEC monetizes directly through high‑value transactions, which explains its appeal to financially motivated groups.
Infrastructure and preparation: BEC vs Phishing
How to identify and defend from BEC and Phishing
The common weakness in both attacks is the human element. Technology helps, but it cannot compensate for broken processes or untrained staff. Effective defenses include:
Treat email as an identity channel: enforce strong authentication and monitor for look‑alike domains.
Harden payment workflows: require out‑of‑band verification for banking changes and multi‑party approvals for high‑value transfers.
Detect infrastructure early: monitor newly registered domains, suspicious TLS certificates, and hosting patterns.
Train for context: phishing awareness reduces clicks; BEC defenses require executive awareness and procedural discipline.
What to Collect for an Investigation?
If you have been affected by BEC or phishing, investigators or law enforcement will typically require:
Timeline: when the incident occurred and how it was first identified.
Entry point: which inbox, form, or channel was used.
Communications: emails, messages, headers, phone numbers, and identities used by the attacker.
Infrastructure indicators: domains, URLs, applications, or portals involved
Authentication: any MFA or one‑time passcodes used.
Financial details: bank accounts, payment rails, or cryptocurrency exchanges involved.
Please note, accurate, early collection of this information can significantly improve the chances of tracing funds or disrupting follow‑on activity.
Conclusion
Phishing and Business Email Compromise are often discussed together but treating them as interchangeable threats leads to blind spots in both prevention and response. Phishing is optimized for scale and visibility; it depends on infrastructure, automation, and volume. BEC is optimized for credibility and timing; it exploits trust, process gaps, and legitimate access.
From an investigative standpoint, this distinction matters. The indicators you look for, the evidence you collect, and the controls that stop the attack are fundamentally different. Blocking domains and URLs may disrupt a phishing campaign, but it will not stop a compromised executive mailbox from authorizing a fraudulent payment.
Organizations that understand this difference—and design their defenses accordingly—are far better positioned to detect attacks early, limit financial impact, and support effective investigations when incidents occur.
Links I read to write the blog
Infrastructure
1) Easy Phishing Infrastructure Setup for Red Teaming
BEC
2) What Is Business Email Compromise (BEC)? - Palo Alto Networks
3) What is Business Email Compromise (BEC)? | Microsoft Security
4) Business Email Compromise Statistics 2026 (+Prevention Guide) - Hoxhunt
Phishing report
1) Phishing Trends Report (Updated for 2025)
FBI
1) Internet Crime Complaint Center (IC3) | Business Email Compromise: The $55 Billion Scam
3) Business Email Compromise — FBI
What LE need from the report
1) Internet Crime Complaint Center (IC3) | FBI Guidance for Cryptocurrency Scam Victims
CISA report
1) Phishing Guidance: Stopping the Attack Cycle at Phase One
How to generate an investigate phishing campaign
1) A Hands-On Investigation into Phishing Campaigns
2) How To Create An Effective Phishing Campaign In 8 Steps
Social engineering 101
1) What Is Social Engineering? Examples + Prevention | CrowdStrike