Vibe Coding: Hype, Reality, and What It Actually Means
Most AI projects don’t fail because of the model — they fail because the knowledge base behind it is messy, outdated, or impossible to retrieve from. Before embeddings, vector databases, or fancy architectures, the real work starts with how your documents are written, structured, and indexed.
In this piece, I break down what it actually means to prepare a knowledge base for AI agents in security, compliance, and risk environments. We’ll look at when indexing really matters, how to structure documents so AI can retrieve answers faster, and why clear titles, meaningful tags, and proper chunking often outperform more complex solutions.
I also share practical examples, a simple readiness checklist, and lessons learned from building AI systems that had to stand up to audits and incident reviews — not just demos.
If you wouldn’t trust a document in an investigation, your AI shouldn’t either.
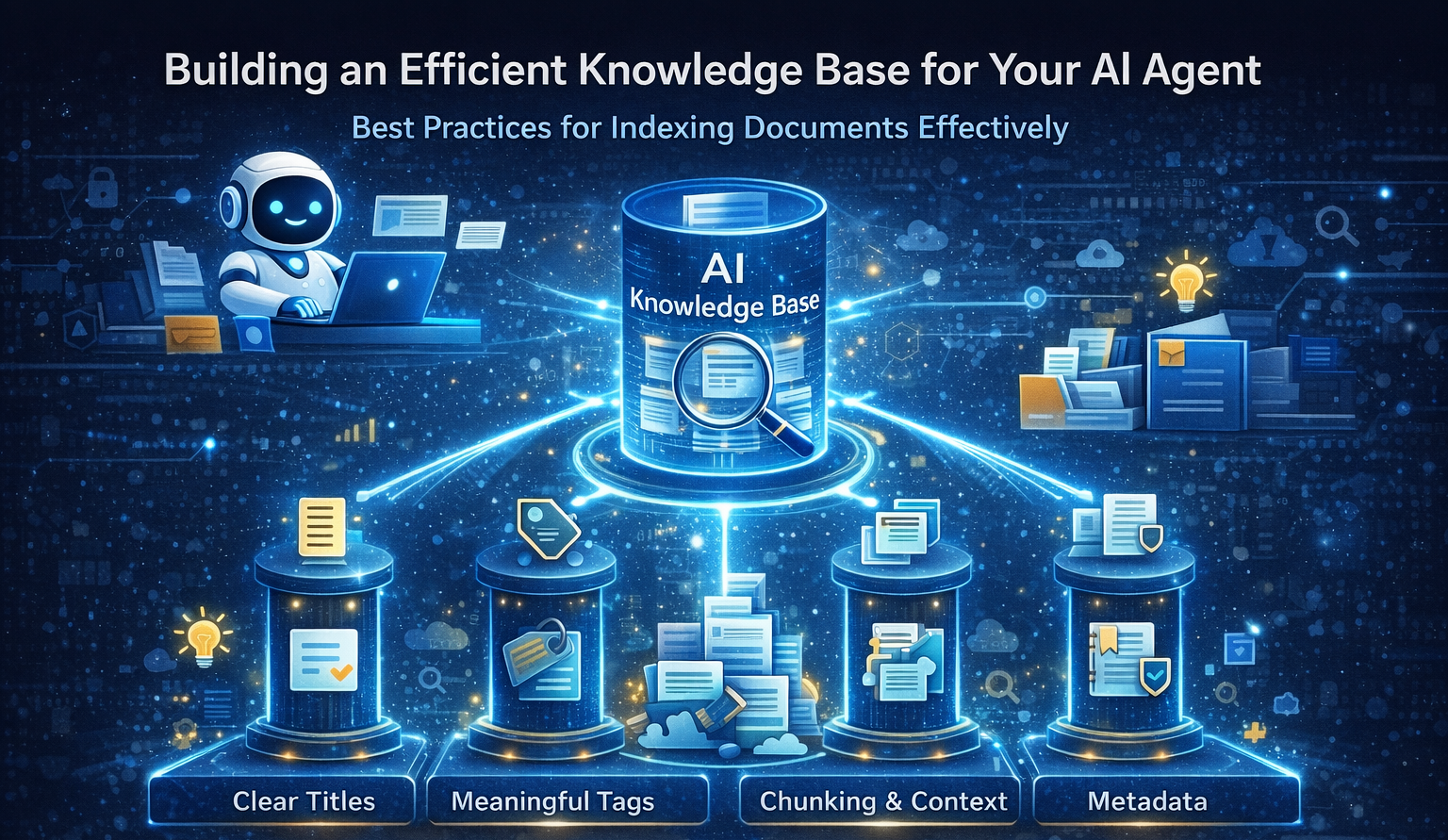
Building AI Knowledge Bases That Actually Work
Most AI projects don’t fail because of the model — they fail because the knowledge base behind it is messy, outdated, or impossible to retrieve from. Before embeddings, vector databases, or fancy architectures, the real work starts with how your documents are written, structured, and indexed.
In this piece, I break down what it actually means to prepare a knowledge base for AI agents in security, compliance, and risk environments. We’ll look at when indexing really matters, how to structure documents so AI can retrieve answers faster, and why clear titles, meaningful tags, and proper chunking often outperform more complex solutions.
I also share practical examples, a simple readiness checklist, and lessons learned from building AI systems that had to stand up to audits and incident reviews — not just demos.
If you wouldn’t trust a document in an investigation, your AI shouldn’t either.
How AI is Connecting Analysis, Threat Hunting and Cloud Investigations
Security, fraud, and cybersecurity teams face a growing challenge: protecting increasingly complex environments shaped by cloud adoption, AI, and IoT, while threats evolve faster than ever. Bad actors are also leveraging AI to scale and accelerate their attacks.
AI is no longer optional, it has become essential. When used correctly, AI can improve security posture and operational efficiency, not by replacing people, but by connecting critical security functions and breaking down silos.
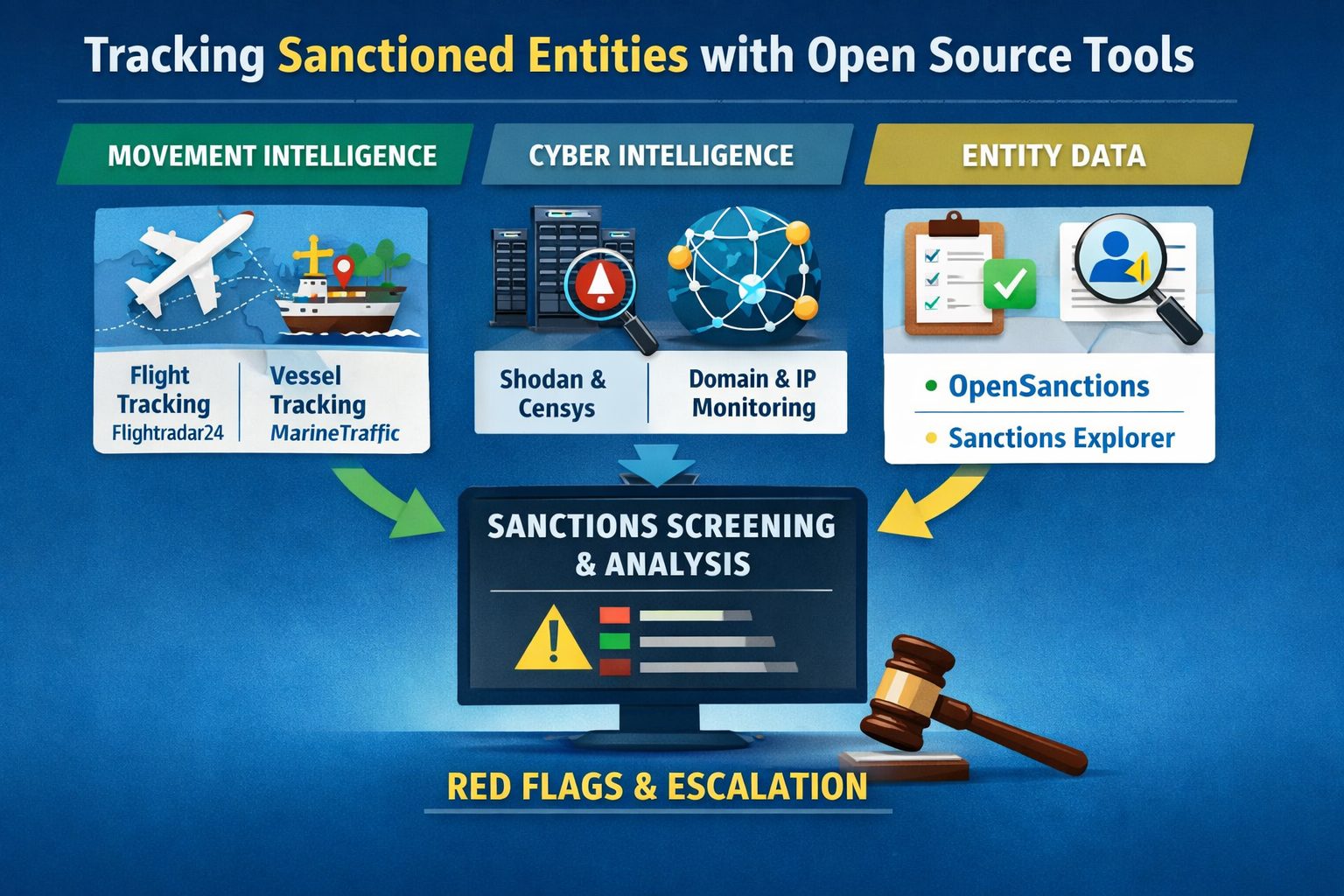
How to Use Open‑Source Tools to Monitor Sanctioned Entities and Individuals
Open source tools—flight and vessel trackers, internet scan engines, and aggregated sanctions lists—can surface early, actionable signals for sanctions monitoring when layered together, documented, and used within legal limitations.
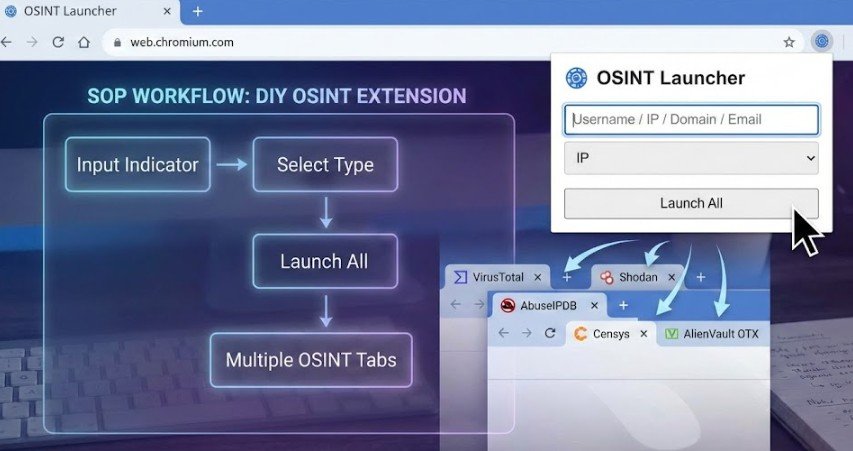
Tab Fatigue? Build Your Own OSINT Launcher Extension
Build your own OSINT browser extension
Differences between Business Email Compromise and Phishing or Spear Phishing
Understand the difference between Phishing and Business Email Compromise
Risk vs Threat: A Practitioner’s View
Understand the difference between risk and threat in cybersecurity, cloud investigations, fraud, and threat intelligence and why it matters to the business.
Fraud vs. Abuse: Why the Difference Matters
Understand the difference between fraud and abuse in cloud platforms.